NFT-Related Attacks
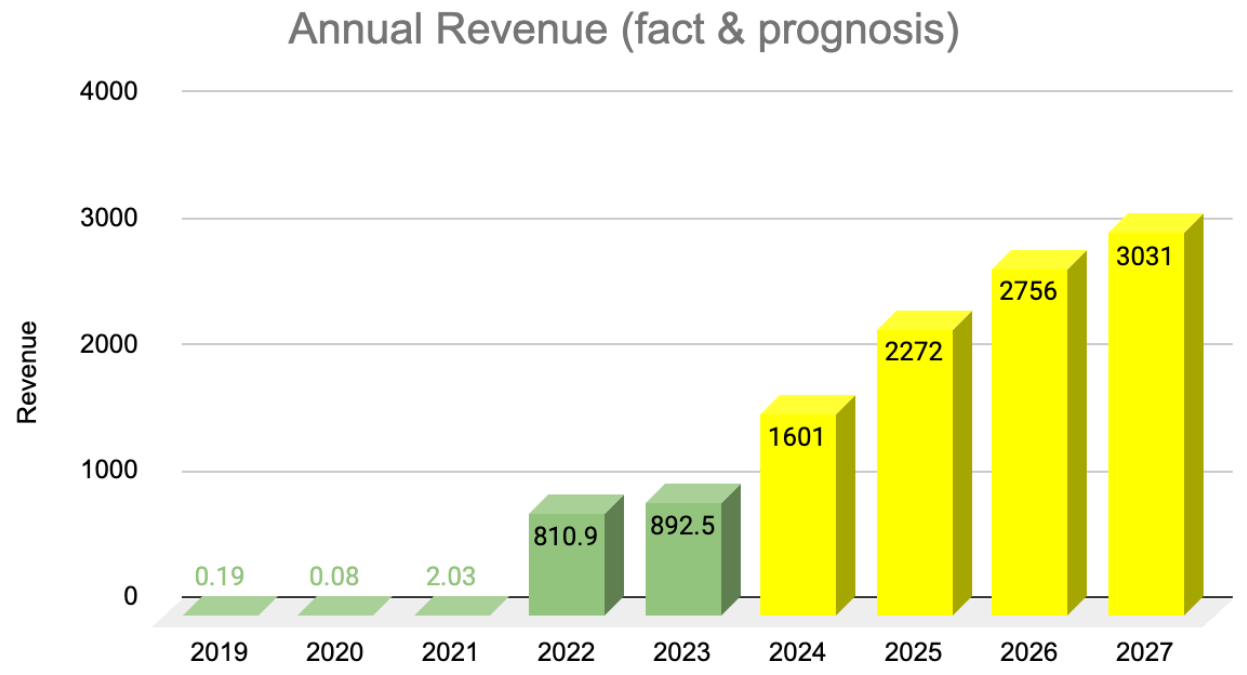
NFT Revenue (2017 - 2023+)
Global NFT Market is enourmous. According to Statista The revenue of the NFT collections has already reached $1.7B since 2017 and will reach $11.36B by the end of 2027.
NFT-Related Crime Volumes
Where there is big money, there is crime, scam and fraud. According to Elliptic already by the mid 2022 the volume of NFT-related crime has reached $0.5B and has been constantly growing since then.
NFTs are be used for money laundering. A user can purchase a comparatively cheap NFT and then list it for an incredibly high price. Another user familiar with the first one of-line buys the token and transfers the amount without taxes, bank fees, or notice of criminal police. Because the buyer's and the seller's accounts are anonymous, such deals can hide bribery to public officials, celebrity payments, or other grey financial operations.
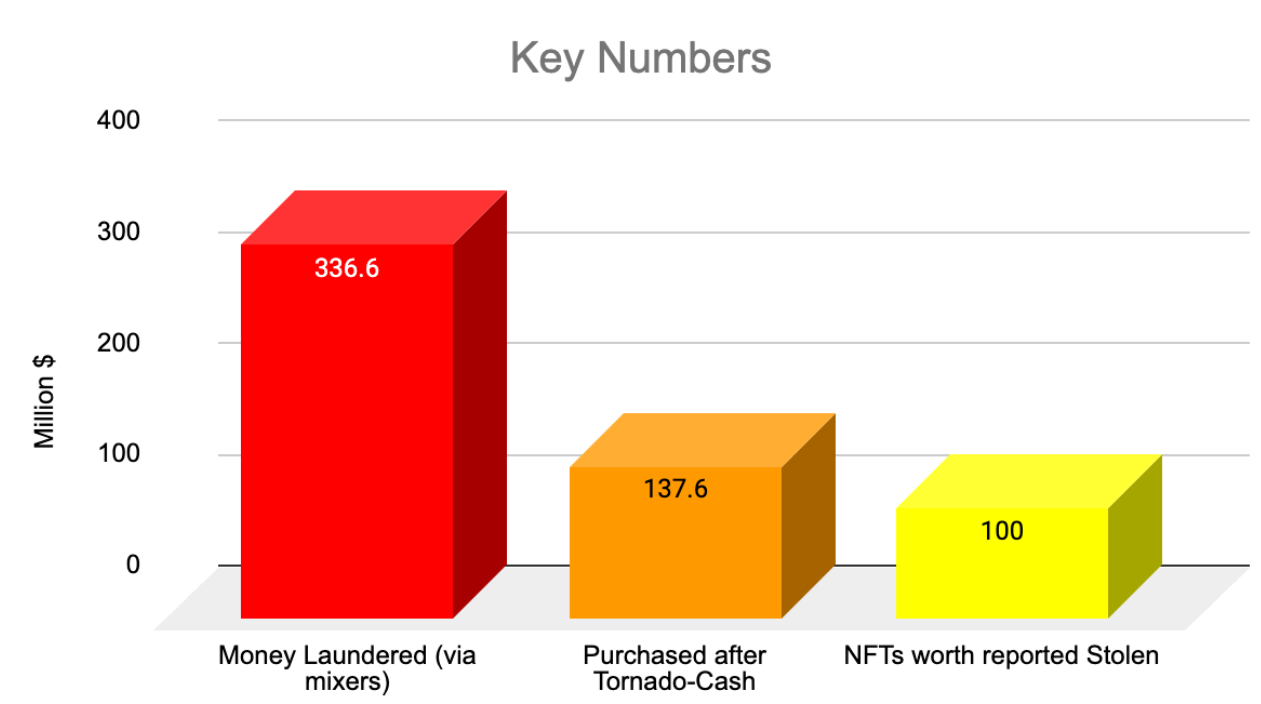
- worth of NFTs were involved in money-laundering schemes
- worth of NFTs were bought via anonimous accounts who received their money from Tornado Cash - a famouse token mixer.
- worth of NFTs were reported stolen by their legitimate owners
Off-Chain NFT Attacks
All the off-chain NFT-related attacks can be divided in two goups:
- Social engineering and
- Technical attacks.
| Social Engineering Scams | Technical Attacks |
|---|---|
| - Recovery Assistance Scams - Impersonation scams - Market Ramping - Influencer pump & dump - Rug Pulls & Exit Scams - Swap Scams | - Social Media Hijacking - Spoofing / Plagiate NFT - Marketplace API Exploits - Frontend Attacks - Airdrop Exploits / Trojan Horse NFTs |
Social Engineering Scams
While there's very little we can do to protect the userf from social engineering attacks but inform and warn about such hazards there is something that can be done to protect from the tech-related attacks.
Recovery assistance scams
Once already scammed NFT owners start complaining and publicly reporting their scams, they fall into the sphere of interest of yet another group of attackers. Their bots infiltrate hundreds of NFT communities and wait in an ambush until a "wounded" victim starts "bleeding." The higher the cost of the lost asset, the more the victim is eager to pay for its recovery. The scammers claim to be highly proficient and have a long record of successful recoveries. They ask for advance payment and vanish after getting it. Sure enough, nobody is even trying to recover a stolen NFT.
Impersonation scams
In this attack, impersonators pretend to be members of the NFT collection creators and NFT marketplaces of crypto wallets. They hunt their prey in the support channels of the corresponding teams and suggest going private to help the users with their problems. In a private conversation, they ask the users for their account credentials, such as wallet seeds or private keys. If the victims believe the impersonators, they hand over the keys to their wallets and lose everything they had there.
Market Ramping
An NFT collection team uses several addresses they control and purchase their NFTs via those accounts creating an impression of a high-volume collection. Users outside the team may notice the trend and buy those NFTs with a "good" sales history at even higher prices. But, to their surprise, they cannot sell those NFTs to any other third parties. If the collection has no utility, such as staking, farming, or other benefits from holding an asset, the users who were the last to buy are left with useless tokens.
Influencer pump & dump
Some NFT collection teams hire celebrities to promite their collection. Kim Kardashian, Paris Hilton and Justin Biber were among the celebrities pumping NFT collections. Since the celebrities were not truly involved in the project after recieving their share of the reward, they soon removed all the traces of the NFT promotion from their social media effectively dumping interest and prices of the tokens.
Rug Pulls & Exit Scams
Some NFT project teams never plan to implement their promises to the community. They hype the collection by promising generous rewards to the asset owners and once they have collected enough money, they shut the project down and hide away from the public. A vivid example of a rug-pull NFT project is Evolved Apes. After the team collected $2.7M, they disappeared.
Swap Scams
Even though such applications like Swap Kiwi can be legitimate themselves, they can be used by scammers to trick owners of expensive (hundreds of thousands of USD worth) NFTs for worthless ones or minuscule amounts. Social engineering is out of our scope because there is very little we can do when a legitimate owner transfers an asset to a thief. The NFT offered for a swap can either be a forgery or a very expensive one, or its price can be pumped by selling to affiliated accounts.
An alternative attack involves adversary-created websites mocking famous ones where users are tricked into calling the
approvefunction in the NFT contract, effectively controlling the contracts by criminals' legitimateoperatorsof the asset. After that, the criminals can transfer NFTs to themselves since they already have the original owner's permission.
Protection:
- Go to the project website and check whether your NFT is on sale.
- Find the real Discord, Twitter & Collection Marketplace.
- Compare the blockchain address of their genuine collection and the one offered to you.
Technical Attacks
This group of attacks usually comprises frontend, backend, or blockchain vulnerability exploits.
Social Media Hijacking
| Usual Channels: | Discord, Twitter, Telegram |
|---|---|
| Techniques: | |
| Social engineering | phishing emails, fraudulent admin accounts |
| Bots Vulnerabilities | plugins’ vulnerabilities allow for privilege escalation |
| Account Compromise | password breach of unprotected by 2FA accounts |
- DM or group announcements too good to be true
- Sense of urgency or limited supply provoking FOMO (fear of missing out)
- Push the victims for irreversible actions with their funds
Protection from Social Media Hacks
Collection Team- When Hacked:
- Inform the users about the hack
- Take back the account control
- Find & remove the hacker
- Communicate - you’re in control
- Be transparent and confident
Collection Team - After a Hack
- Communicate & earn sympathy
- Consider the victims
- Rebuild your community
- Prevent your channel from hacks
User Protection Against Scams
- Disable DMs (direct messages)
- Only add trusted “friends”
- Turn 2FA whenever possible
Signs of a scam
- “Too good to be true” == Scam
- Urgent & limited offers == Scam
If you notice signs of a scam
- Take your time to double check
- Find the real community and ask
NFT Plagiarizm
- NFTs are tokenized records managed by smart contracts. They consist of on-chain & off-chain part. Their content is public and is open to copying.
- It is easy to check in each chain which contract has been deployed first. The timestamp in the NFT minting transactions can help distinguish the genuine ones from the fake copies, but as long as they are on one chain.
- Scammers often go to other chains and even other protocols, and mint exactly the same collection. Especially notorious is OpenSea contract.
- According to the Marketplace itself, 80% of the NFTs minted their are fake duplicates of the famous collections.
Marketplace API Exploits
- A marketplaces UI interacts with a backend API.
- The backend can be compromised and all the data can go to the hackers.
- NFT Listing & delisting happes via this API.
- NFT listings can be changed from high to incredibly low rates and bought by the scammers for pennies.
Mitigation:
- List only on established Marketplaces who care about security
- Check your collections’ listings & prices on daily basis
- Join the marketplace community & support group for emergency cases
Frontend Attacks
- In January 2022, OpenSea - the biggest NFT marketplace UI was hacked.
- The hacker got away with ETH 332 ($ 800,000 at the time).
Trojan Horse NFTs
- A hacker crafts and gifts a malicious NFT to their victims
- Victims interact with the NFT, a pop-up window with a third party wallet opens asking the user to log-in
- Once victims connect their wallet the hacker gets access to their private key
The method used in this attack is called steganograhpy. This attack can be implemented via all media channels: text/code, image, video, or audio. Adversaries can use this type of attack in two ways:
a. to hide malicious code that can be launched on a victim's machine b. to extract and send sensitive data from the user's machine to the attacker's computer.
- Text steganography can be injected in the smart contract code of the NFT presented to a user via a giveaway or a pretend "erroneous" transfer to a "wrong" user.
- In an image steganography, attackers inject malicious JavaScript code in the image of the NFT, which runs when the new asset owner opens it in the browser. Depending on the image format type, bits or pixels are invisibly replaced with malware code. Several known tactics include
bit masking,filtering,pattern encoding,andcosine transformation. - In Audio steganography, hackers usually exploit
WAVfiles to conceal their malware.2 - Since a video file is a stream of images accompanied by audio, technics 2 and 3 are used in video steganography.
Preventing steganography:
To prevent steganography, there are WEB3 and general cybersecurity mechanisms:
WEB3 developers can deploy the NFT assets on immutable storage servers such as IPFS (Inter-Planetary File System), where the asset's CID (Content ID) is a hash of its contents. As long as the content of the asset file results in the same hash using the same hashing algorithm, the file is authentic, and its integrity is guaranteed. Unless the original collection creators injected their assets with malware, the NFT owner is safe.
In case NFTs include in-game assets sitting on compromised centralized servers, hackers can stuff the NFT assets with their malware and attack the collection owners once they view their assets in their browsers.
XP.NETWORK's smart contract whitelisting is one of the mitigation tools against NFT contracts containing malicious code trying to attack the users or the bridge.
Among traditional cyber security measures against steganography can be:
- Remove all the structured metadata that might compromise confidentiality or conceal trojans.
- Remove all unused data, making random noise at the pixel level.
- Optimize the bitmap data using a compression algorithm. It will automatically remove the unused bits that contain the malware.
- Do not sign in with your crypto account to unfamiliar wallets.
- Make a research about the wallet and its reputation in the market.
- Look for the red flags: no info, contradictory info, security related reports
Audio steganography is used mostly to transfer secret information by hiding it in a public WAV file that anyone can hear. Still, only the designated recipients know how to extract the hidden data from the files.